According to Verizon, email fraud (spoofing) accounts for more than 90% of enterprise attacks. Why is email such a popular vector for spreading malware and malicious links? Because it’s much easier for criminals to convince a human to click on a fraudulent file or link within an email than it is to force their way into a hardened infrastructure.
Think about it this way: Would you rather take on a tank or trick the crew into coming out of the tank and surrender? The latter option is much easier.
The structure of email
Why can’t we just harden email like we do a firewall and turn it into a tank? Because email wasn’t built with security in mind. It was invented in the 1960’s and the original standard, RFC 822, was written in 1982. Updated standards weren’t written until 2008, which contain the current email structure that we all know and are comfortable with.
Email as we know it today consists of three major sections:
- The envelope
- The message header
- The message body
Each email program handles email differently, so they all speak a common language, Simple Mail Transport Protocol (SMTP), to allow these different systems to talk to each other.
In many ways, email is like a letter that we might mail. However, the recipient of the email doesn’t see the envelope. In most cases, that’s fine because when we compose an email in our email clients, the envelope information usually gets filled in from the header information automatically.
However, when spoofing an email, a threat actor can put whatever they want into the following fields:
- Mail from:
- From:
- Subject:
- Date:
- To:
- Reply-To:
Why are they allowed to do that, and how does email spoofing work? Let’s explore an example.
How to spoof an email:
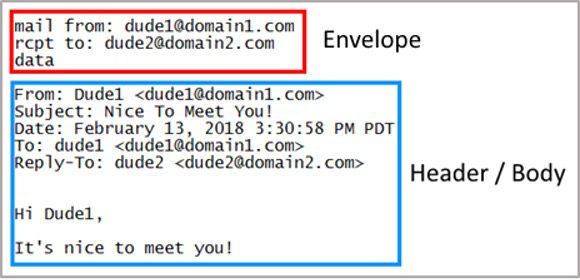
The box in red above highlights the email’s envelope. Usually, the envelope fields are filled out for the sender automatically during the translation of the header. Neither the sender nor the recipient usually sees this information. The stuff in blue is the header and body. The Email Body is the stuff you normally see when you open an email delivered to you.
It is possible for a sender to tinker with the message header and spoof the sender’s identity so that the email looks like it is from someone other than Dude1. Let’s break down how spoofing an email’s identity works.
Say you have a friend that likes to play practical jokes on you. And you receive an email from them that says this:
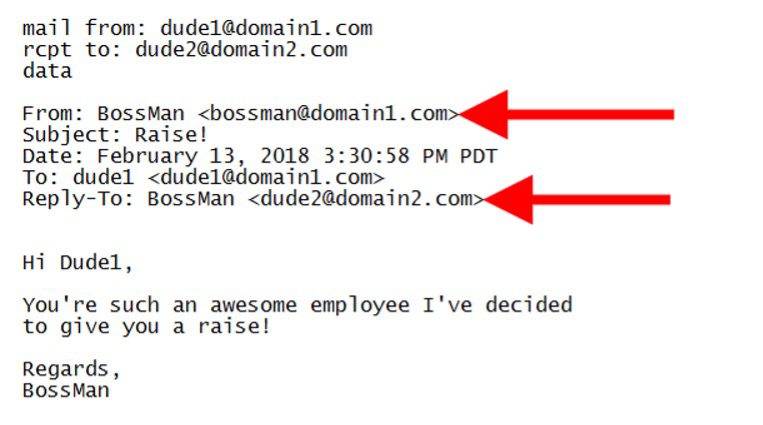
Notice that the envelope fields are correct, but the From and Reply-To are false. When Dude1 receives this email, he may think it’s from his boss. When he hits “Reply,” all he’ll see in the To: field is the “BossMan” name, but it will go back to his friend who spoofed the email, Dude2.
Cyber criminals can cleverly disguise an email in the same way and custom tailor it for their intended victims
For example, if a criminal wants banking credentials from their target, they can do the same thing Dude2 did, but instead of telling Dude1 that he got a raise, they can falsely represent themselves within the email as a trusted bank and direct the recipient to go to a fraudulent website.
Email spoofing success relies on human vulnerability
There are many variations of this email scam, however, at the core, they are the same: spoof the sender’s identity and convince the victim the email is not from a threat actor but a legitimate source. From there, the end goal is usually the same, extracting money from the victim.
LeafTech’s Solutions
Though we can’t stop these bad actors from trying to spoof our company, LeafTech does have a solution to warn you when an email may be spoofed! Our next-generation Email Spam Filtering also intelligently analyzes the full content of the message, including the hidden headers, to look for strange discrepancies like a different sender listed in the ‘mail from:’ and ‘From:’ sections. If your system didn’t alert you that the recent bad actor was spoofing contact@www.leaftechit.com, and flag the email as possible phishing – give us a call, and we’ll help upgrade your email security and continue to serve and protect your team.
720-319-8324 x.2 – support@www.leaftechit.com – www.LeafTechIT.com